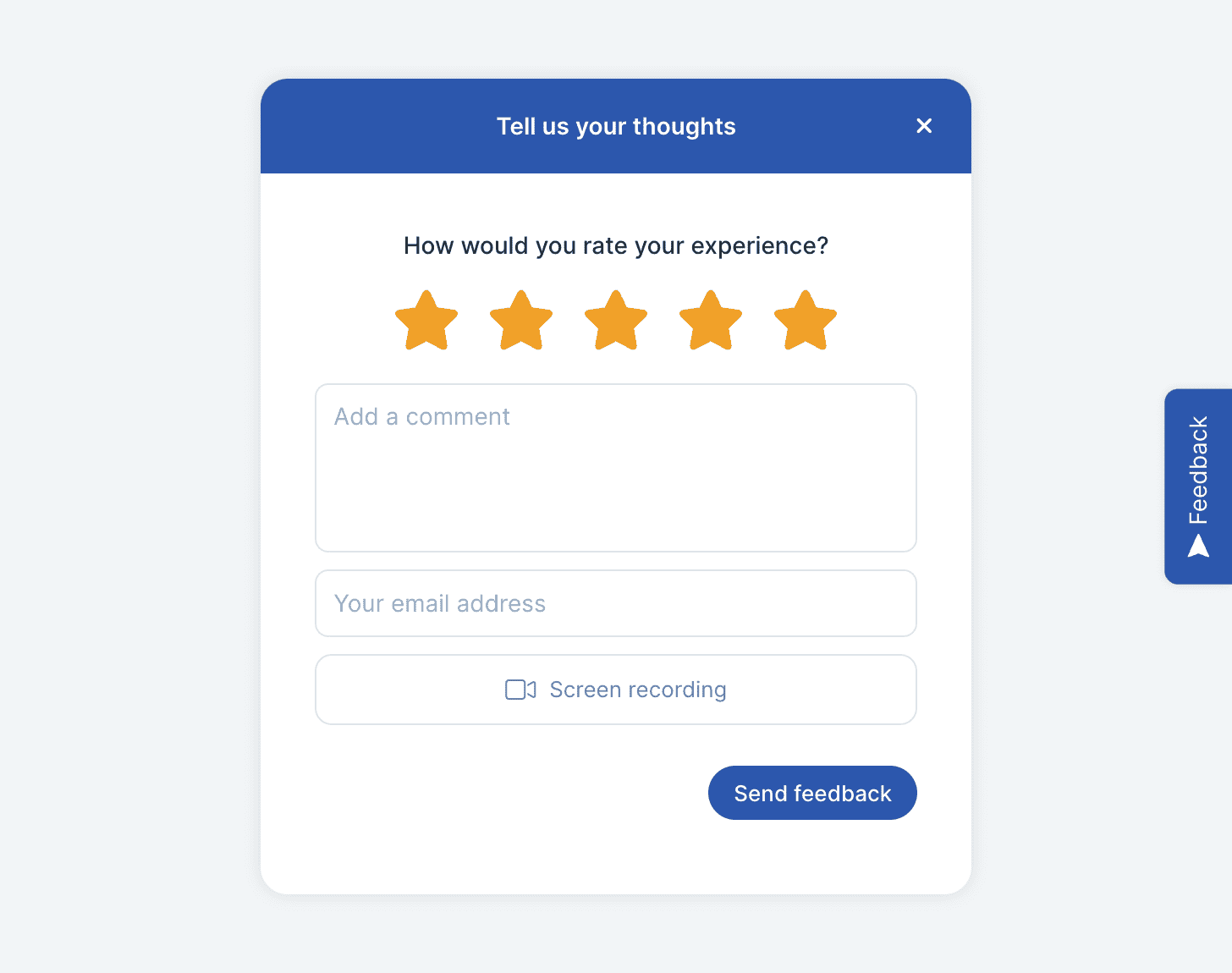
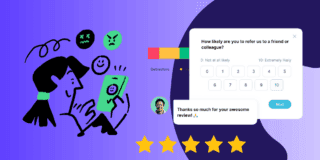
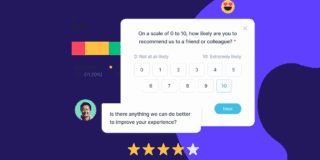
In the complex and ever-evolving digital environment, cybersecurity is not merely a convenient addition; it is a fundamental necessity. This is especially true for product managers, who shoulder the weight of ensuring digital products are not just user-friendly but also resilient against cyber threats.
Far from a niche concern, understanding and implementing best cybersecurity practices is critical for anyone shepherding digital projects through the life cycle. In this article we’ll explore the ‘why’ behind integrating cybersecurity into product management and how you, as a product manager, can fortify your resource against the cyber storms lurking on the horizon.
Why is Cybersecurity Important In Product Management?
Let’s be clear… cybersecurity is not just for the IT guys. It’s in the DNA of digital assets which is also the realm of product management. The role of a product manager is complex, encompassing the visioning and management of the product roadmap, feature prioritization, monitoring of progress, and guiding the product towards success. Yet amongst all this, if cybersecurity isn’t prioritized from the outset, the whole project is at risk of falling apart.
Ensuring Trust with Consumers
In a world laden with data breaches and online vulnerabilities, consumer trust is elusive. Product managers are akin to the guardian of this trust, ensuring that every decision made aligns with best practices, protecting user data from unauthorized access or misuse. Trust, once lost, is challenging to regain, making active cybersecurity a non-negotiable point in product development.
Regulatory Compliance Alignment
The legislative landscape is morphing in response to the growing cybersecurity concerns. GDPR, CCPA, HIPAA, and other regulations have teeth, and non-compliance is a costly oversight. Product managers must understand and enforce frameworks and standards within their products to meet these regulatory requirements.
Strategic Risk Management
Product managers excel at managing risk. By integrating cybersecurity from the outset, risk management becomes proactive. Effective risk management is more than risk avoidance; it’s about understanding the threats and having a robust plan in place to mitigate them.
Start now with Userback.
Get started with a 14-day free trial.
What Common Challenges Do Product Managers Face Regarding Cybersecurity?
The battleground of cybersecurity is sprawling, with new challenges emerging as old ones are vanquished. Product managers must be vigilant and adaptive to steer their products away from these risks.
Balancing Security with Innovation
One of the greatest challenges is balancing the need for security with the pressure to innovate. At times, these needs may seem antithetical, but product managers harmonizing them can ensure products are both cutting-edge and secure.
Sustaining Awareness and Preparedness
Cybersecurity isn’t a static entity; it’s a nimble, evolving target. Product managers need to stay abreast of the latest threats and technologies to be adequately prepared to defend their products.
Nurturing a Culture of Security
Cybersecurity isn’t just about technology; it’s about people. Product managers must foster a culture where every team member appreciates the gravity of security. This requires constant advocacy and education.
What Role Do Product Managers Play In Cybersecurity?
Product managers are the linchpin in the cybersecurity values chain, connecting the security team to the development process. They must marry strategic oversight with tactical implementation.
Setting Clear Security Objectives
Product managers must translate the goals of cybersecurity into tangible product requirements. This means setting clear security objectives and ensuring they are met.
KPI Tracking and Reporting
Just as with any aspect of product management, what gets measured gets improved. Product managers must establish key performance indicators for cybersecurity and report these back to relevant stakeholders.
Incident Response Coordination
When—rather than if—an incident occurs, product managers spring into action, coordinating the response efforts to minimize damage and ensure that the product’s integrity is maintained.
How can Userback Help Maintain Cybersecurity Best Practices?
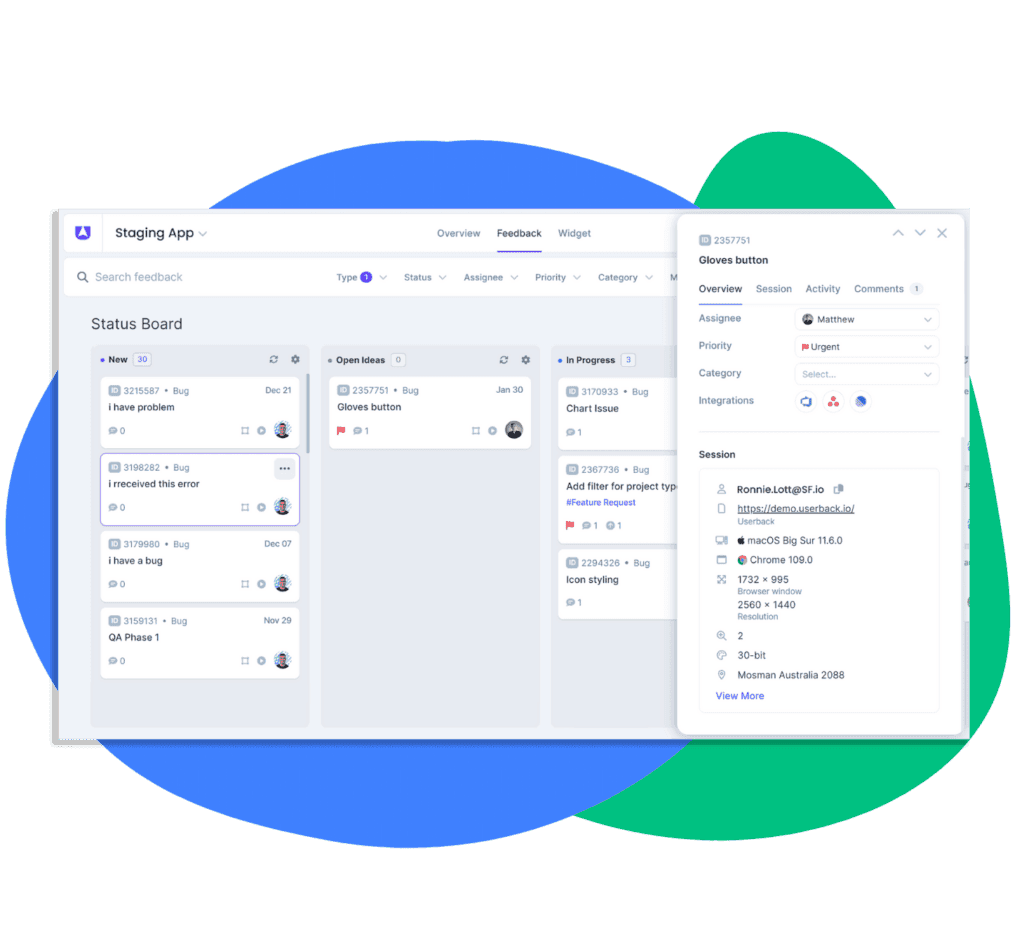
Enter Userback—an ally for the vigilant product manager in the battle for cybersecurity supremacy. With its suite of user feedback tools, Userback seamlessly integrates with your product management approach, helping you forge products that are secure from their very foundations.
Streamline Feedback Collection
Gone are the days of clunky feedback loops. Userback lets you harvest user insights with unprecedented ease, ensuring that no stone is left unturned in your quest for a secure and user-friendly product.
Prioritize Security Enhancements
Userback goes beyond gathering feedback—it helps you decipher the priority of security enhancements. By enabling you to understand the severity and potential impact of reported issues, Userback ensures that your resources are optimally allocated.
User-Driven Security Protocols
When users feel like part of the process, the security of their data becomes personal. With Userback, you can communicate the changes in security protocols transparently, building a user base that champions your product’s security as fiercely as any compliance officer.
Conclusion
The digital landscape is fraught with potential hazards, and product managers are its vigilant custodians, orchestrating every plot and navigating every twist. Cybersecurity is not merely an optional theme; it’s an essential narrative thread that must weave through every line of code, every screenshot, and every user interface. By embedding cybersecurity best practices into your products, you’re not only averting risks; you’re cultivating a legacy of trust and dependability.
Utilize Userback’s tools to not merely endure in the digital world, but to flourish—safely. Product managers, the moment to act is now. With Userback at your disposal, the future is as secure as your aspirations are boundless.
Secure your products; secure your future. The digital world awaits, and with Userback, you’re ready.
Are you ready to safeguard your products’ future? Start free with Userback and see first-hand how it can revolutionize your approach to product security.